is a protocol used to transfer data between to entities (client and server or services) using encryption. It's basically a
where data is transferred over a secure channel. This means that all data transmitted in both directions is secure from eavesdropping. In software development it is used to securely connect to a remote git repository, a test- and production server etc. A SSH client should be already installed on a UNIX systems (such as Linux or MacOSX).
The SSH protocol
You can use SSH to log into the remote server, transfer files and execute commands. Before you do this, you have generate a key pair on your local computer. SSH uses asymmetrical cryptography (or public-key cryptography). The so called private key (or secret key) is used for encrypting the data, while the public key is used for decryption and vice versa. Hence this key-pair is generated from the same random data. Asymmetrical algorithms are not very fast, compared to symmetrical cryptographic algorithms. Symmetrical algorithms use a single key that is shared between both sides (client and server) to encrypt the transmitted data. Hence, SSH uses public-key cryptography only for authentification (to prove that the client is allowed to access the server) and to exchange a new key (session key) that is used to encrypt and decrypt connection between client and server. Here symmetrical cryptographic is being used. The secret key is stored securely on your computer and should be never ever given to anyone else. The public key is be distributed publicly, e.g. to the remote server you want to access.
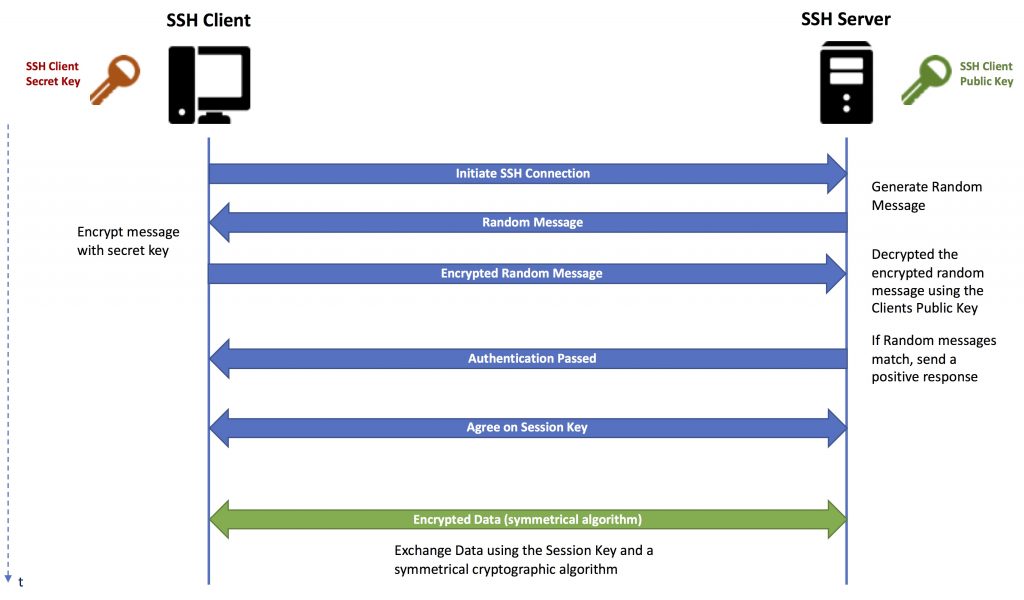
This image shows a simplified version of the SSH protocol with client authentification (usually client and server agree on the encryption algorithms and other parameter, Diffie-Hellman is used for session key generation and exchange and more). However, this simplification should be sufficient to understand the basics you need to know as a software developer.
Generating SSH Keys
First check if you haven’t already generated a SSH key-pair by looking into the .ssh folder in your home directory
ls ~/.ssh
If the directory is not present or doesn’t contain something like: id_rsa, id_rsa.pub you need to generate a new key-pair by using
ssh-keygen
You are being ask for the key-store directory and a passphrase (a password which can also contain spaces). I did not use any special algorithms here, so in my case RSA with a key-length of 2048 bit was used (which is considered to be a sufficient key-length for a strong security). In the image below you might notice the SHA-256 and fingerprint. SHA256 is a so called hash-function, A hash-function is a one-way function which calculates a fixed-length value (hash-value) out of a arbitrary sized data. One-way means that you can’t re-create the original message from the hash-value. The result is often called a fingerprint (a compressed value of my key in this case).
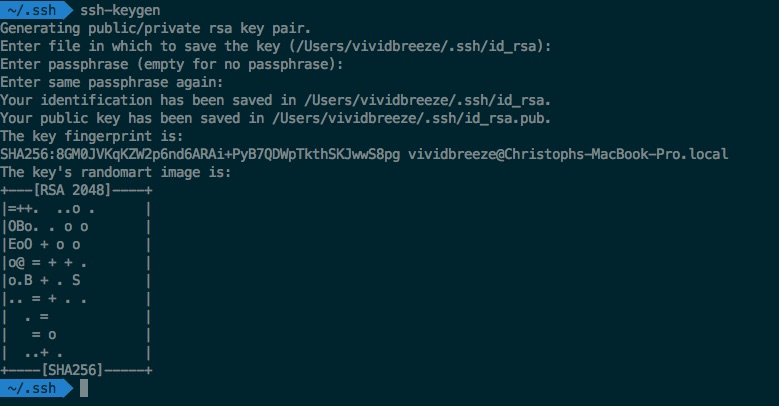
If you want to use other cryptographic algorithms, you can do so by using the -t option, e.g. if you want to use DSA
ssh-keygen -t dsa
to change the key-length, use the -b parameter
ssh-keygen -t rsa -b 4096
The keys (id_rsa, id_rsa.pub) should now be visible in the ~/.ssh directory. The secret key (id_rsa) is protected by the pass-phrase. You can upload the public key (id_rsa.pub) to the remote server or service you want to connect with, e.g. a git-Repository. If you have root access to the remote server you have to store the public key in.~/.ssh/authorized_keys.
You can also let ssh-keygen in a script without the need of a pass-phrase
ssh-keygen -f $HOME/.ssh/id_rsa -t rsa -N ''
- Hackintosh – The Hardware - 22/02/2020
- Installing Artifactory with Docker and Ansible - 17/08/2018
- Docker Networking – Overlay Network - 15/08/2018
One Comment
Comments are closed.